Self-Sovereign Identity is a concept in the digital movement that only the user should own their identity data fully without intervention from outside administration. COVID-19 has created a situation where everyone tries to digitize their day-to-day activity to reduce human contact. With that we have faced the biggest challenge of protecting our identity. This is the reason that we must move to the era of Self-Sovereign Identity, below we will its benefits.
USING A SELF-SOVEREIGN IDENTITY
Recently I had to go to the bank and cancel my card, due to some fraudulent transactions recorded by third parties. When the bank requested me to confirm whether I have provided my bank credentials to those third parties, I wasn’t able to do that because I couldn’t remember where I had given my bank details. Simply, I didn’t have control over my identity with those third parties.
With the emergence of the internet throughout our day today lives, and the rapid increase of online usage increases issues such as data theft, online fraud, and especially identity theft.
When you interact with online businesses to buy things you normally have to trust some third parties to fulfill your actions. Most of the time these third parties are service providers. Sometimes we provide our details to these third parties to make purchase transactions on our behalf. One of the more frightening aspects of this is third parties collect confidential details from a lot of people and make them one sole target of hackers.
Due to the increasing usage of the internet and the necessity, we can’t stay away from using our details. Due to the current situation of COVID-19, digitalization is very important.
Similar actions conducted in person do not represent the same amount of risk. For example, if someone asks you to verify your identity, we show our ID or driver’s license, and when you pay at the store, you provide your bank card. In this way, the control and the ownership of the data stays with you. The verifier accepts this because it is a verifiable credential, and this person doesn’t have access to all the details where the driver’s license or bank card was issued. This is the Self-Sovereign Identity, however, we need a digitized version of this.
By using Self-Sovereign Identity, the individual identity holders no longer have to seek permission from a centralized authority or intermediary, and can thus control their data and credentials completely.
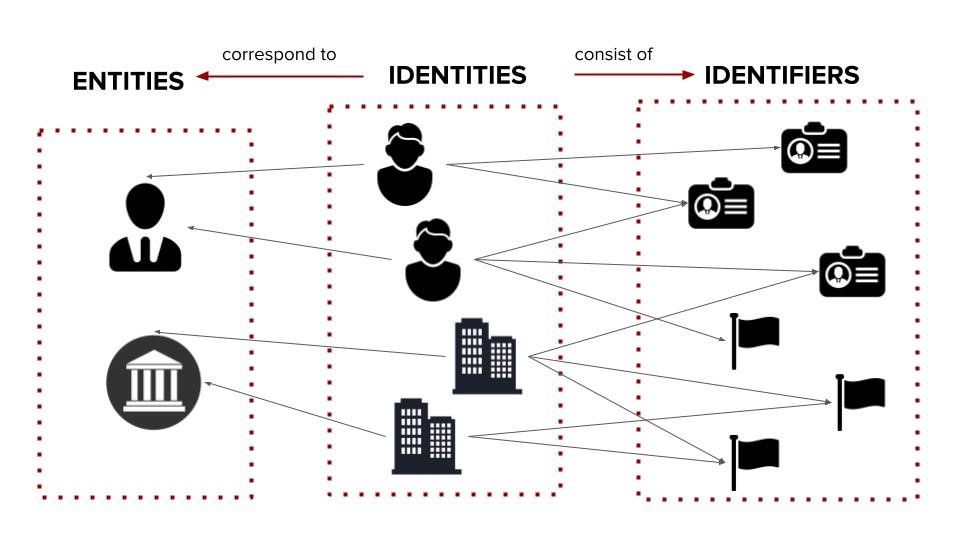
Relationship between entities, identities and identifiers
VERIFIABLE CREDENTIALS (VC) AND DECENTRALIZED IDENTIFIERS (DIDs)
Verifiable Credentials (VC) are an open standard for digital credentials. They represent the electronic equivalent of the physical credentials that we all have, such as a driver’s license, ID card, passport, etc. One of the great advantages of these verifiable credentials over physical credentials is that they are much more reliable and secure.
This can be explained using the following example:
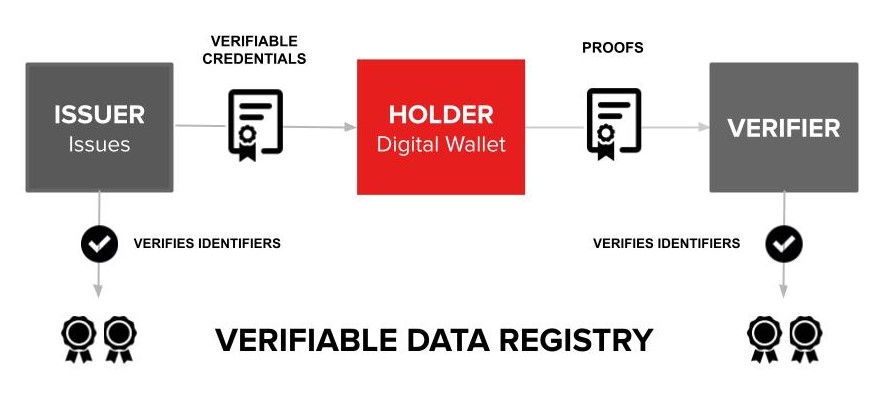
Verifiable credential ecosystem
Behind these verifiable credentials we have a set of claims that are bound to the credentials. These claims identify and represents the person, allowing them to be the sole owner with access to that sensitive information. You can present these claims and requests for a verifiable credential from an authorized issuer, and it will be verified cryptographically by the verifier.
For example, a credit card is a traditional and physical verifiable credential. When you request a credit card from an issuer (i.e. an authorized bank) you have to present several documents; your bio data, your salary information which are claims that represent the subject. When you use this credit card for payments at a store it verifies your identity through this card without presenting your personal confidential information.
Digitizing this concept rather than using a physical card, enables the use of cryptography. The most common concept for this is to have a digital wallet which can be accessed only by you. This doesn’t mean this is the safest way and users should be vigilant in protecting their data, but it reduces the risk of exposing centralized identity details of a lot of users. This is where decentralized identifiers come into the picture.
Decentralized Identities (DID) are the key element of Self-Sovereign Identity. These types of identifiers offer enhanced security, as they allow the identity to be digital, verifiable and decentralized. Additionally, these identifiers allow the DID controller to control and disassociate itself from central registries, i.e. from any of the certified authorities or identity providers.
VERIFIABLE CREDENTIAL BASED AUTHENTICATION VIA OPENID CONNECT
OpenID Connect is an identity layer in the OAuth 2.0 protocol based on authentication from an authorized server, that allows users to obtain information and verify the identity of the end user. In technical terms, OpenID Connect specifies a RESTful HTTP API, using JSON as a data format.
WSO2 Identity Server can act as an OpenID provider. OpenID provided by WSO2 Identity Server can be used to sign-in and sign-up for external services. Also, WSO2 Identity Server acts as an OpenID consumer. Any OpenID can be used to sign-in and sign-up for the WSO2 Identity Server. WSO2 provides connectors to connect with more verifiable registries.
The OpenID provider will ask for a username or password as a primary means of verification, however, this can be improved to the level of using biometric authentication using mobile phones. Next OpenID providers issue an identity token with the requested information. The information contained in this token is similar to the details printed on your credit card.
There is a way to improve this further by using Verifiable Credential Authentication with OpenID Connect (VC-AuthN OIDC). Because the above model OpenID provider becomes centralized and has more control over the data, the details available within OpenID provider can authenticate access to another site or service. This is a feature of federated identity and it violates the concept of Self-Sovereign Identity.
VC-AuthN OIDC uses the OpenID connect standards to easily integrate with the supported systems and also provides a way to authenticate using the verifiable credentials, giving the control back to the user. This is similar to the traditional OpenID connect, the only difference is in the token information. Rather than using the user’s information to construct the token, this uses claims in the verifiable credentials presented by the user.
HOW BLOCKCHAIN FACILITATES SELF-SOVEREIGN IDENTITY
The evolution of Identity Management moving toward a user-centric control approach. Self-Sovereign Identity evolved more with the popularity of blockchain technology. Blockchain doesn’t only solve the above-mentioned challenges, it provides the missing link to use cryptography to prove identity.
Let’s use an example to explain this. The bank is the issuer of the claim holder which is your credit card. And the bank will link the decentralized identifier on the blockchain that signs the claims via keys. Your digital wallet, which holds your claims, has keys that link to the decentralized identifier controlled on the blockchain. You can use that to countersign the credit card. The store as the verifier can determine whether this is issued by the bank and that it belongs to you. This is the usage of blockchain to look up decentralized identifiers.
CONCLUSIONS
With the evolution of Identity Management, we have reached the era of user centric Self-Sovereign Identity. This gives back the control again to the user and makes it more real like a digital world. This makes digitization more secure and reliable for the users, which is a necessity in everyday life and especially during a pandemic.