In this article we tell you what you need to know about Adaptive Authentication, as well as the challenges that companies face when trying to provide access to multiple devices
What is adaptive authentication?
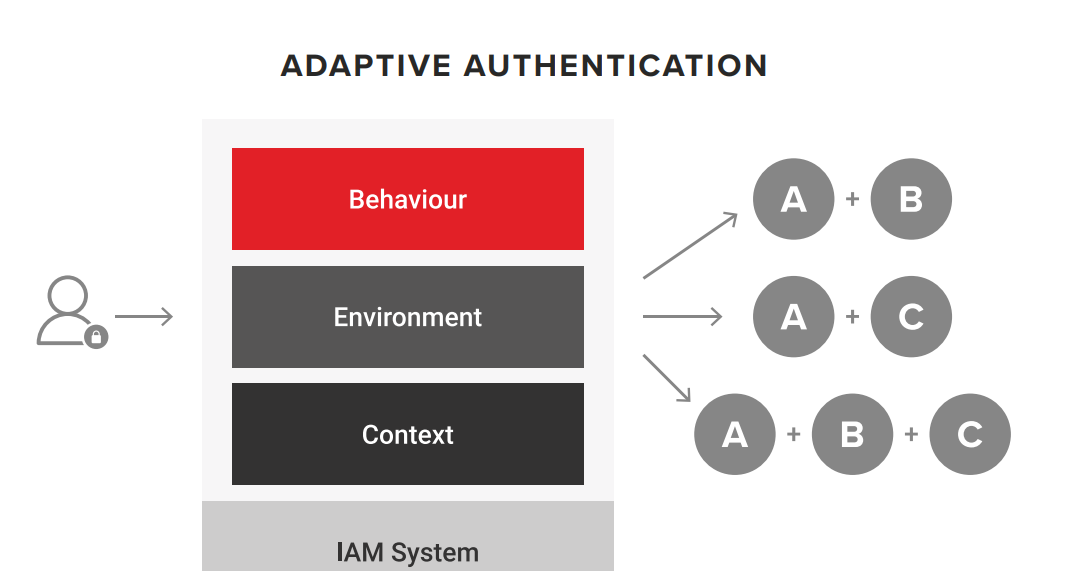
Primary use of adaptive authentication is to adapt the security measures on the account to the risk-level of the user. User risk levels are governed by granular admin policies and behaviours.
Adaptive Authentication is a flexible method of setting up two factor authentication (2FA) and multi-factor authentication (MFA) which would allow different security factors to be used based on a user’s risk factors. Practically, this means that the right level of authentication is applied to the right users:
- For low risk users, this means that when they log into an account, they may just have to use 2FA with an SMS/E-mail code sent to their device.
- For high risk users, they would need to use a biometric scan to log into the same account. This improves security by making sure that high risk users and accounts have the right level of adaptable, flexible security.
Adaptive Authentication is far more advanced than traditional MFA. It can respond to the device that login attempts are made from, the IP address and the location of login attempts, so that it can identify when a login attempt is high-risk, and therefore implement stronger authentication parameters.
-This article may also interest you to understand more about adaptive authentication: Intelligent adaptive authentication: everything you need to know-
Current state and challenges for the adaptive authentication
Business landscapes are transforming, along with a workforce that is increasingly modernizing where and how they work. Let’s take a look at the challenges that businesses face when it comes to providing access to multiple devices whilst maintaining secure authentication.
Managing a virtual Workforce
With the current pandemic situation organizations are forced to adapt to working remotely. The workforce needed to be mobile, so employees expect access to their applications and devices from anywhere. This change determines who is accessing what data, on which device, on which network. Each touch point poses a security threat, especially third-party apps.
Managing passwords
Account lockouts, password resets, and regular password rotation can only lead to frustration. On average, your team spends a significant amount of time on password management-related issues alone. In addition to the resource drain, this often results in employees resorting to poor practices such as password reuse, documenting passwords on a phone, and emailing or sharing passwords. Each weak or shared password presents a risk to the company; it can result in a data breach and loss of company data.
Every 4 cases out of 5 identity incidents are because of credentials breach [based on Verizon’s DBIR].
Gaps in Technology and Compliance Visibility
As more employees bring new tools into the workplace, IT can get left out of the loop on critical applications that entire teams may use to manage company data. It’s important to understand who has access to applications and data, where they are accessing it, and what they are doing with it. You need central visibility and control across all your systems.
New buying patterns
This as we know is an emerging trend and has led to an increasing range of experiences powered by digital services and smartphones that includes one-click buying, QR-based payments and Scan & Go. Building customer trusts and moving them to new buying behaviour through digital services has always been a challenge.
If you want to know how Chakray can help you in your journey with Adaptive Authentication, then contact us!








