Identity and Access Management is used not only for security requirements, but also for the success of your business. Identity Analytics can be used to identify the behaviours and patterns of the users and events and those findings can be used to reduce the cost of your business, increase risk awareness and responsiveness, improves compliance, inform behavioral-based access policies, provide rich user experiences, enhance employee productivity and invest on new business paradigms to succeed your business.
The below index shall be followed:
|
|---|
1. What is Identity Analytics?
Identity Analytics is the process of analysing the vast amount of identity and access management data in your organisation using various techniques. Even you can use advanced technologies like machine learning and artificial intelligence (AI) technologies to consume and analyse these identity and access management data. Identity analytics can be used for enhancing existing identity and access management processes using user activity and event data, fraud detection, threat analysis and real-time monitoring and alerting.
Mainly these are two ways that you can analyze identity and access management data:
- Batch analysis is processing large amounts of gathered data during certain periods of time.
- Real-time analysis is processing real time data.
These can be used for many purposes like threat analysis, predictive analysis, fraud detection and implementing risk based authentication. Both batch analytics and real-time analysis can be used for the success of your business.
2. How can you use Identity Analytics for your business success?
Identity Analytics can be used to analyze data about user activities and make important decisions about your business to improve your business. Organizations can get an idea about following indicators using identity analytics and those can be used to improve your business and get new business leads.
- Customer growth over time
- Number of customers and customer growth by geographical region
- Number of customers by age and profession
- Frequently used business functions
- Favorite modes of business like web or mobile application
- Conversion rate of existing customers to online customers over time
- Access patterns
- Details about local login attempts
- Details about federated login attempts
- Session statistics
- Statistics about business events
These analytics can be used to the success of your business as below.
2.1 Make important decisions about the business
These identity and access management analytics can be used to make valuable decisions about the growth of your business. By analyzing existing identity and access management data using machine learning algorithms and artificial intelligence techniques to predict future events will be very helpful to make informed decisions regarding customers and services for the future.
Identity analytics helps decision makers like CIOs and CISOs to understand and predict the impact of identity and identity management using the analytics information gathered as below.
- user behaviour
- key factors of relevance to them (e.g. costs, risk exposure, reputation, trust, etc.)
As an example business decision makers can decide when you need to perform marketing campaigns and what is the interested audience by using identity analytics. This interested audience can be identified using the number of customers categorized by geographical region, age and profession.
2.2 Secure all aspects of your business
These are some of the most common types of cyber attacks that happen even today.
- Denial of Service: A Denial of Service (DoS) attack disrupts its normal function of a service and prevents other users from accessing it. Normally in this case overwhelm the computing resources and cause it to crash.
- Phishing: Phishing attacks are used to exploit and extract valuable information of the organization. Phishing messages will be sent to users using an email, SMS message or other form of communication inorder to trick them into revealing confidential information such as usernames, passwords or downloading malware into their device.
- Malware: Malware includes a variety of harmful software including viruses, ransomware, spyware, and more.
- Ransomware: Ransomware is a form of malware that encrypts your local files on the infected device. In order to obtain the encryption key to access your files, the attacker will demand payment.
Identity analytics can be used to identify and prevent these kinds of attacks mentioned. These are some of the solutions that can be implemented within the organization depending on the identity analytics:
- Anti-Phishing mechanics
- Anti Password brute force attacks
- Detecting compromised attacks
- Detecting anomalies in user behaviour
It is very important to secure your organization from cyber attacks in order to maintain the reputation of your business, gain the trust of your customers, save cost and time.
Identity analytics can be used not only to prevent attacks but also to improve the security flows and security process of your organization. As an example by looking at the access patterns identified from identity analytics can be used to identify where additional security measures will be needed. At the end, identity analytics can be used to reduce the risk and improve the security compliance.
2.3 Improve user experience
By analysing the user behaviours using identity and access management data such as access and login patterns can be used to improve the user experience and this will help to attract more customers. As an example by looking at identity analytics, it is possible to identify the what are the places that user’s spend more time on automated processes and those pain points can be improved inorder to give seamless experience to the users.
2.4 Enhance identity and access management processes
Identity analytics based on historic and current data can be used to enhance the identity and access management processes of your organization in order to cater to organizational and business needs. This will help to attract more customers, increase sales, save the cost and time within the organization and more importantly identify best security procedures that match your business and organizational needs.
As an example, Identity analytics can be used to improve or enhance following processes in order to get above mentioned benifits.
- Define organization threat model
- Simplify role management process
- Improve access request and approval process
- Monitoring specific accounts
- Define process to handle untrusted data
2.5 Improve employee productivity and satisfaction
In addition to finding what works for customers, identity analytics can be used to get insights about the best strategies for improving productivity in the workplace. Using the analytics, companies can get a better idea about exactly how their employees work, what are the work processes that consume more time and money and delays in the processes. With these facts organizations can understand how they can support their employees to drive productivity to the next level. Also they can invest money on improving the organizational processes and automate the processes where necessary to achieve more productivity within the organization and this will help to improve employee satisfaction. At the end, all these things will help to succeed as a business.
2.6 Implement risk-based authentication
Identity analytics can be used to dynamically manage access decisions as well as intelligently identify and manage user risk profiles based on application usage. This reduces the manual effort required and increases the accuracy of security operations.
Identity analytics can be used to assess end users’ risk score using transactional data and that score can be used to implement adaptive authentication. Adaptive authentication is an evolved form of Multi-factor Authentication (MFA) where authentication steps can be configured and deployed in such a way that the system would decide which steps to prompt during the authentication process depending on the user’s risk profile and the behaviour. Attributes identified from the analytics data such as region or location, device type, age of the user, time of the day can be used to implement adaptive authentication inorder to improve the security as well as user experience.
2.7 Fraud detection and prevention
Identity analytics can be used to define the behavioral baselines of normal user activities and anomalies can be identified using that baseline.Traditional fraud rules and statistical models are no longer sufficient to detect the fraudes in today’s complex environments. Domain knowledge can be derived from the historical data using predictive analytics and current data using real-time analytics. This can be used to identify the frauds and anomalies of the activities.
Fraud detection involves monitoring the behavior of users in order to estimate anomalous behavior. Fraud prevention is also a very important fact, same as fraud detection. Fraud prevention occurs before the fraud attempt and the goal of fraud prevention is to reduce the risk of future fraud.
Machine learning algorithms and artificial intelligence can be used to identify frauds and anomalies. As an example, machine learning algorithms can be used to model the normal behaviour of the events and then anomalies can be detected as deviations from the modelled normal behaviour in real time.
2.8 Threat analysis
Threat analysis is a process of determining which components of the system need to be protected and the types of security threats that these components should be protected from.
Organizations can define a threat model using identity analytics such as number of active users of the system, number of super users in the system, geographical distribution of users, behavioural patterns of the users. Also artificial intelligence and machine learning can be used to define these theart models using analytics data.
2.9 Increase business agility and speeds innovation
Business agility is the ability of an organisation to adapt quickly to market changes and respond rapidly to customer demands. Business agility is a very important thing to not only to survive in the business but also to succeed in the business. Decision makers can get an idea about the market trends using identity and analytics patterns, usage of services, age of the users, geographical locations and many other factors involved in identity analytics. With these details in hand, organizations can overcome business challenges and get the competitive advantage.
Also organizations can use identity analytics to speed the innovation within the organizations not only within the identity and access management domain but also within the whole organization. Organizations can identify the user favourites with access rates, pain points for both customers and employees using the analytics. Depending on these facts organizations can invest time and money for innovations where necessary and it will help to growth and success of the business in the long run.
3. WSO2 Identity Analytics
WSO2 Identity Server Analytics is a lightweight processing platform that allows you to collect events, analyze them in real-time, identify patterns, map their impacts, and communicate the results within milliseconds. Mainly WSO2 Identity Server can be configured to publish authentication related events to WSO2 Identity Server Analytics so that you view and analyze the identity and access management data. These are two main analytics that can be achieved using WSO2 identity analytics:
- Login analytics: Includes statistics related to login attempts made via WSO2 Identity Server.
- Session analytics: Includes statistics related to specific sessions that get created for different applications accessed via WSO2 Identity Server.
These are some of the out of the box WSO2 identity server analytics features
| Type | Chart/Widget | Purpose |
| Login attempts over time |
|
Deriving the login patterns and detect deviations that may due to unusual occurrences such as attacks, system downtime, etc |
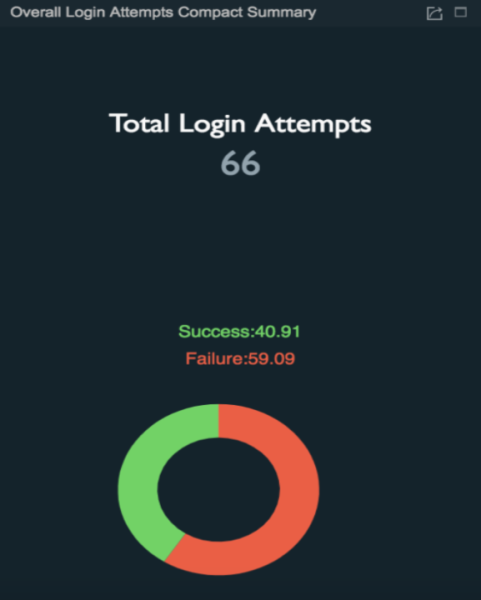
| Compact summary of login attempts |
|
Identifying the percentages of the successful and failed login attempts. |
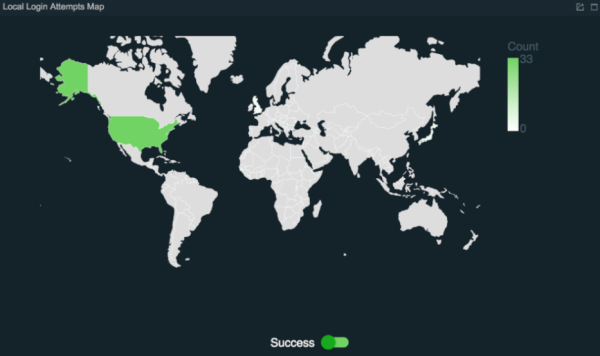
| Map view of login attempts |
|
Viewing the countries from which the logins were attempted.
Indicates the number of login attempts. The success attempts and failure attempts. |
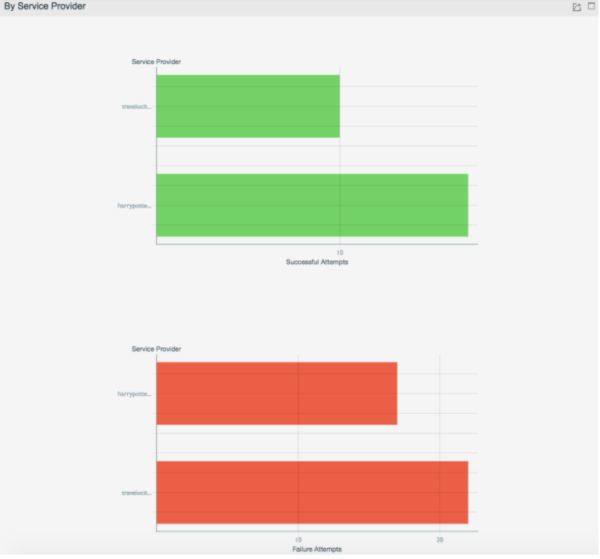
| Details of login attempts by service Provider | The successful and failed login attempts sorted by service provider | Viewing the login attempts sorted based on the service providers |
| Details of login attempts by identity provider | The successful and failed federated login attempts sorted by identity provider. | Viewing the federated login attempts sorted based on the identity provider. |
| Details of login attempts by user, user role and user store |
|
Viewing the login attempts sorted based on the user names, user roles or user store domains. |
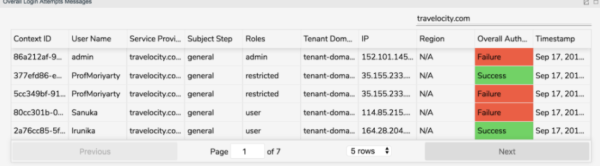
| Full details Of each login attempt | Presents details of each login attempt including the context ID, user name, service provider, subject step, roles, tenant domain, IP, region, whether the overall authentication was successful or not, and the time stamp. | View the details of each login attempt. |
| Session count over time | The Session Count Over Time
(The number of active sessions over the selected time interval, The number of sessions that were started during the selected time interval, The number of terminated sessions over the given time interval) |
Understanding the current load that is handled by your application in terms of the number of active sessions at any given time.
Understanding the load handled by your application in terms of the number of sessions over any selected time interval. Compare the load handled in terms of the number of sessions over different time intervals to identify patterns relating to the usage of your applications. |
These are some of the WSO2 Identity Server Analytics charts and widgets listed above.
- Local login attempts map based on IP address
- Details of overall login attempts
- Successful and failed login attempts sorted by service provider
- Compact summary of overall login attempts
- Overall login attempts over time
All these comprehensive sets of WSO2 Identity Analytics features can be used to achieve business success. Few examples of how you can use the WSO2 Identity Analytics can be used to the success of your organization are listed below.
- Decide when you need to perform marketing campaigns and what the audience is by looking at login attempts over time, compact summary of login attempts, map view of the login attempts, etc.
- Organizations can overcome business challenges and get the competitive advantage with these comprehensive sets of WSO2 Identity Analytics. Also organizations can decide in which areas and when you need to invest for innovations using these WSO2 Identity Analytics.
- By using WSO2 Identity Analytics, organizations can get an idea about overall security of their business and then they can take necessary actions to implement and enhance security in all areas of the business by reducing the risks and enhancing the compliances.
- Fraud detection involves monitoring the behavior of users and events in order to estimate anomalous behavior. WSO2 products have the capability of implementing fraud detection and alerting capabilities by implementing rules with WSO2 Streaming Integrator and Identity Analytics.
- Threat models can be defined for organizations based on the organizational requirement based on WSO2 Identity Analytics.
- WSO2 Identity Analytics capabilities of monitoring user patterns and processes can be used to improve the user experience as well as improve employee productivity.
- Risk based authentication can be implemented using identity analytics by analysing additional properties of the user, which are available during login such as login device, geolocation, IP address, etc. Based on these properties, a risk score is calculated for the user. This risk score is classified and based on the severity level, and additional authentication factors such as Email verification, SMS-based verification, prompting CAPTCHA are requested.
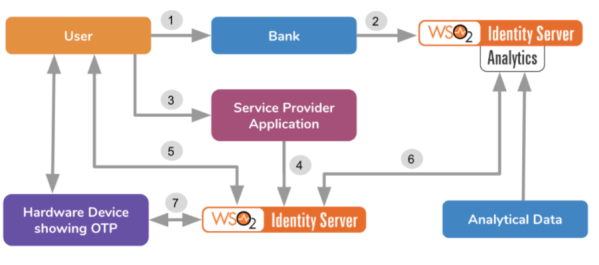
Risk profiling flow: WSO2 source
4. Conclusion
Identity Analytics is a must have in your organization in order to achieve the business goals and increase your business growth. You can manage the identity and access management of your organization effectively using WSO2 Identity Server while using its analytics capabilities for the success of your business.
WSO2 Identity Server and Identity Analytics are fully open source solutions with a comprehensive set of identity and access management capabilities and identity analytics capabilities.








