In this article, we will explore how Lynis and Ansible work and how they can be used to evaluate the security of your systems. In addition, we will offer advice on how to improve your security. We will also look at how you can automate process with Ansible.
Finally, we will take a look at how you can create more aesthetically pleasing HTML reports in order to present the results of your audits from Lynis in a clear, and understandable way.
To do so, we’ll explore the following points:
|
1. Lynis installation
Lynis is an open code tool used to carry out security audits for operating systems based in Unix, such as Linux and macOS. Lynis takes place in the determined system and scans the system to check for vulnerabilities and unsafe configurations. After the scan, Lynis provides a detailed report with recommendations on how to improve system security.
To use Lynis, you first need to download it and decompress it in your system. Then, you can use it with the command “lynis” followed by any parameter option that you wish to use. For example, to scan the entire system and generate a report, you can use the command “lynis audit system”. Lynis also has lots of parameter options that can be used to carry out more specific scans or to personalize the auditing process.
1.1 Lynis installation from the web
To install Lynis onto a Linux system from the web, follow these steps:
vagrant@master:~$ wget https://downloads.cisofy.com/lynis/lynis-2.7.5.tar.gz
Decompress the Lynis file using the tar command:
vagrant@master:~$ tar zxpvf lynis-2.7.5.tar.gz
1.2 Installation from repository
The second option is to download it from the official repository. Download the Lynis source code from the Git repository using the following command:
vagrant@master:~/repo$ git clone https://github.com/CISOfy/lynis Cloning into 'lynis'... remote: Enumerating objects: 14638, done. remote: Counting objects: 100% (44/44), done. remote: Compressing objects: 100% (31/31), done. remote: Total 14638 (delta 21), reused 30 (delta 13), pack-reused 14594 Receiving objects: 100% (14638/14638), 7.77 MiB | 16.85 MiB/s, done. Resolving deltas: 100% (10787/10787), done.
Navigate the directory decompressed in Lynis:
vagrant@master:~/repo$ ls lynis vagrant@master:~/repo$ cd lynis/
2. Audits
Once installed, you can carry out your first system audit. The test that we are going to carry out is a clean installation of Ubuntu. This will affect our analysis and the report which we will generate. We recommend carrying out a report before and after in order to compare the results. To carry out our first audit, we need to follow these steps:
Step 1. Go to the directory you have generated and execute the following script. You will see the available options.
vagrant@master:~/lynis$ ./lynis [ Lynis 2.7.5 ] ################################################################################ 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ################################################################################ [+] Initializing program ------------------------------------ Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under the terms of the GNU. See the LICENSE file for details about using this software. Usafe: lynis command [options] command:
audit
audit system : Perform local security scan
audit system remote <host> : Remote security scan
audit dockerfile <file> : Analyze Dockerfile
show
show : Show all commands
show version : Show Lynis version
show help : Show help
update
update info : Show update details
Options:
--no-log : Don't create a log file
--pentest : Non-privileged scan (useful for pentest)
--profile <profile> : Scan the system with the given profile file
--quick (-Q) : Quick mode, don't wait for user input
Layout options
--no-colors : Don't use colors in output
--quiet (-q) : No output
--reverse-colors : Optimize color display for light backgrounds
Misc options
--debug : Debug logging to screen
--view-manpage (--man) : View man page
--verbose : Show more details on screen
--version (-V) : Display version number and quit
Enterprise options
--plugindir <path> : Define path of available plugins
--upload : Upload data to central node
More options available. Run './lynis show options', or use the man page.
No command provided. Exiting..
Step 2. To scan the entire system you have the following options.
vagrant@master:~/lynis$ ./lynis audit system
Step 3. Initializing the program
[+] Initializing program
------------------------------------
###################################################################
# #
# NON-PRIVILEGED SCAN MODE #
# #
###################################################################
NOTES:
--------------
* Some tests will be skipped (as they require root permissions)
* Some tests might fail silently or give different results
- Detecting OS... [ DONE ]
- Checking profiles... [ DONE ]
---------------------------------------------------
Program version: 2.7.5
Operating system: Linux
Operating system name: Ubuntu Linux
Operating system version: 20.04
Kernel version: 5.4.0
Hardware platform: x86_64
Hostname: master
---------------------------------------------------
Profiles: /home/vagrant/lynis/default.prf
Log file: /tmp/lynis.log
Report file: /tmp/lynis-report.dat
Report version: 1.0
Plugin directory: ./plugins
---------------------------------------------------
Auditor: [Not Specified]
Language: en
Test category: all
Test group: all
---------------------------------------------------
- Program update status... [ WARNING ]
===============================================================================
Lynis update available
===============================================================================
Current version is more than 4 months old
Current version : 275 Latest version : 308
Please update to the latest version. New releases include additional features, bug fixes, tests and baselines. Download the latest version: Packages (DEB/RPM) - https://packages.cisofy.com Website (TAR) - https://cisofy.com/downloads/ GitHub (source) - https://github.com/CISOfy/lynis ===============================================================================
2.1 Analysis of the system, plugins, kernel, services.
Some of the checks that Lynis carries out include:
- Review of system configuration: Lynis reviews the configuration of the system and the services to reassure you that they are configured in a way which is safe and optimal.
- Review of the firewall configuration: Lynis reviews the configuration of the firewall to reassure you that it is configured in an appropriate way and that it is protecting the system.
- Review of the password configuration: Lynis reviews the configurations of the passwords to reassure you that they are configured in a way which is safe and that they are not using weak passwords.
- Review of the account configuration: Lynis reviews the configurations of the accounts to reassure you that they are configured in a way which is safe and that they are not using accounts with unnecessary administrative licenses.
- Review of the configuration of files: Lynis reviews the configurations of files to reassure you that they are configured in a way which is safe and that they are not using unnecessary file licenses.
- Review of the configuration of packages: Lynis reviews the configurations of packages to reassure you that they are configured in a way which is safe and that they are not using unnecessary or vulnerable packages.
- Review of the configuration of the network: Lynis reviews the configuration of the network to reassure you that they are configured in a way which is safe and that they are not disclosing sensitive information online.
And lots of other system checks.
[+] System Tools ------------------------------------ - Scanning available tools... - Checking system binaries... [+] Plugins (phase 1) ------------------------------------ Note: plugins have more extensive tests and may take several minutes to complete - Plugins enabled [ NONE ] [+] Boot and services ------------------------------------ - Service Manager [ systemd ] - Checking presence GRUB2 [ FOUND ] - Checking for password protection [ NONE ] - Check running services (systemctl) [ DONE ] Result: found 22 running services - Check enabled services at boot (systemctl) [ DONE ] Result: found 58 enabled services - Check startup files (permissions) [ OK ] [+] Kernel ------------------------------------ - Checking default run level [ RUNLEVEL 5 ] - Checking CPU support (NX/PAE) CPU support: PAE and/or NoeXecute supported [ FOUND ] - Checking kernel version and release [ DONE ] - Checking kernel type [ DONE ] - Checking loaded kernel modules [ DONE ] Found 57 active modules - Checking Linux kernel configuration file [ FOUND ] - Checking default I/O kernel scheduler [ NOT FOUND ] - Checking for available kernel update [ OK ] - Checking core dumps configuration [ DISABLED ] - Checking setuid core dumps configuration [ PROTECTED ] - Check if reboot is needed [ YES ] [+] Memory and Processes ------------------------------------ - Checking /proc/meminfo [ FOUND ] - Searching for dead/zombie processes [ OK ] - Searching for IO waiting processes [ OK ] [+] Users, Groups and Authentication ------------------------------------ - Administrator accounts [ OK ] - Unique UIDs [ OK ] - Unique group IDs [ OK ] - Unique group names [ OK ] - Password file consistency [ SUGGESTION ] - Query system users (non daemons) [ DONE ] - NIS+ authentication support [ NOT ENABLED ] - NIS authentication support [ NOT ENABLED ] - sudoers file [ FOUND ] - PAM password strength tools [ SUGGESTION ] - PAM configuration files (pam.conf) [ FOUND ] - PAM configuration files (pam.d) [ FOUND ] - PAM modules [ FOUND ] - LDAP module in PAM [ NOT FOUND ] - Accounts without expire date [ OK ] - Accounts without password [ OK ] - Checking user password aging (minimum) [ DISABLED ] - User password aging (maximum) [ DISABLED ] - Checking Linux single user mode authentication [ OK ] - Determining default umask - umask (/etc/profile) [ NOT FOUND ] - umask (/etc/login.defs) [ SUGGESTION ] - LDAP authentication support [ NOT ENABLED ] - Logging failed login attempts [ ENABLED ] [+] Shells ------------------------------------ - Checking shells from /etc/shells Result: found 9 shells (valid shells: 9). - Session timeout settings/tools [ NONE ] - Checking default umask values - Checking default umask in /etc/bash.bashrc [ NONE ] - Checking default umask in /etc/profile [ NONE ] [+] File systems ------------------------------------ - Checking mount points - Checking /home mount point [ SUGGESTION ] - Checking /tmp mount point [ SUGGESTION ] - Checking /var mount point [ SUGGESTION ] - Query swap partitions (fstab) [ NONE ] - Testing swap partitions [ OK ] - Testing /proc mount (hidepid) [ SUGGESTION ] - Checking for old files in /tmp [ OK ] - Checking /tmp sticky bit [ OK ] - Checking /var/tmp sticky bit [ OK ] - Mount options of / [ OK ] - Disable kernel support of some filesystems - Discovered kernel modules: udf [+] USB Devices ------------------------------------ - Checking usb-storage driver (modprobe config) [ NOT DISABLED ] - Checking USB devices authorization [ DISABLED ] - Checking USBGuard [ NOT FOUND ] [+] Storage ------------------------------------ - Checking firewire ohci driver (modprobe config) [ DISABLED ] [+] NFS ------------------------------------ - Check running NFS daemon [ NOT FOUND ] [+] Name services ------------------------------------ - Checking search domains [ FOUND ] - Checking /etc/resolv.conf options [ FOUND ] - Searching DNS domain name [ FOUND ] Domain name: local - Checking /etc/hosts - Checking /etc/hosts (duplicates) [ OK ] - Checking /etc/hosts (hostname) [ OK ] - Checking /etc/hosts (localhost) [ OK ] - Checking /etc/hosts (localhost to IP) [ OK ] [+] Ports and packages ------------------------------------ - Searching package managers - Searching dpkg package manager [ FOUND ] - Querying package manager - Query unpurged packages [ NONE ] - Checking security repository in sources.list file [ OK ] - Checking upgradeable packages [ SKIPPED ] - Checking package audit tool [ NONE ] - Toolkit for automatic upgrades (unattended-upgrade) [ FOUND ] [+] Networking ------------------------------------ - Checking IPv6 configuration [ ENABLED ] Configuration method [ AUTO ] IPv6 only [ NO ] - Checking configured nameservers - Testing nameservers Nameserver: 127.0.0.53 [ OK ] - Getting listening ports (TCP/UDP) [ DONE ] - Checking promiscuous interfaces [ OK ] - Checking status DHCP client [ NOT ACTIVE ] - Checking for ARP monitoring software [ NOT FOUND ] [+] Printers and Spools ------------------------------------ - Checking cups daemon [ NOT FOUND ] - Checking lp daemon [ NOT RUNNING ] [+] Software: e-mail and messaging ------------------------------------ [+] Software: firewalls ------------------------------------ - Checking iptables kernel module [ FOUND ] - Checking host based firewall [ ACTIVE ] [+] Software: webserver ------------------------------------ - Checking Apache [ NOT FOUND ] - Checking nginx [ NOT FOUND ] [+] SSH Support ------------------------------------ - Checking running SSH daemon [ FOUND ] - Searching SSH configuration [ FOUND ] - SSH option: AllowTcpForwarding [ NOT FOUND ] - SSH option: ClientAliveCountMax [ NOT FOUND ] - SSH option: ClientAliveInterval [ NOT FOUND ] - SSH option: Compression [ NOT FOUND ] - SSH option: FingerprintHash [ NOT FOUND ] - SSH option: GatewayPorts [ NOT FOUND ] - SSH option: IgnoreRhosts [ NOT FOUND ] - SSH option: LoginGraceTime [ NOT FOUND ] - SSH option: LogLevel [ NOT FOUND ] - SSH option: MaxAuthTries [ NOT FOUND ] - SSH option: MaxSessions [ NOT FOUND ] - SSH option: PermitRootLogin [ NOT FOUND ] - SSH option: PermitUserEnvironment [ NOT FOUND ] - SSH option: PermitTunnel [ NOT FOUND ] - SSH option: Port [ NOT FOUND ] - SSH option: PrintLastLog [ NOT FOUND ] - SSH option: StrictModes [ NOT FOUND ] - SSH option: TCPKeepAlive [ NOT FOUND ] - SSH option: UseDNS [ NOT FOUND ] - SSH option: VerifyReverseMapping [ NOT FOUND ] - SSH option: X11Forwarding [ NOT FOUND ] - SSH option: AllowAgentForwarding [ NOT FOUND ] - SSH option: AllowUsers [ NOT FOUND ] - SSH option: AllowGroups [ NOT FOUND ] [+] SNMP Support ------------------------------------ - Checking running SNMP daemon [ NOT FOUND ] [+] Databases ------------------------------------ No database engines found [+] LDAP Services ------------------------------------ - Checking OpenLDAP instance [ NOT FOUND ] [+] PHP ------------------------------------ - Checking PHP [ NOT FOUND ] [+] Squid Support ------------------------------------ - Checking running Squid daemon [ NOT FOUND ] [+] Logging and files ------------------------------------ - Checking for a running log daemon [ OK ] - Checking Syslog-NG status [ NOT FOUND ] - Checking systemd journal status [ FOUND ] - Checking Metalog status [ NOT FOUND ] - Checking RSyslog status [ FOUND ] - Checking RFC 3195 daemon status [ NOT FOUND ] - Checking minilogd instances [ NOT FOUND ] - Checking logrotate presence [ OK ] - Checking log directories (static list) [ DONE ] - Checking open log files [ DONE ] - Checking deleted files in use [ DONE ] [+] Insecure services ------------------------------------ - Installed inetd package [ NOT FOUND ] - Installed xinetd package [ OK ] - xinetd status [ NOT ACTIVE ] - Installed rsh client package [ OK ] - Installed rsh server package [ OK ] - Installed telnet client package [ OK ] - Installed telnet server package [ NOT FOUND ] [+] Banners and identification ------------------------------------ - /etc/issue [ FOUND ] - /etc/issue contents [ WEAK ] - /etc/issue.net [ FOUND ] - /etc/issue.net contents [ WEAK ] [+] Scheduled tasks ------------------------------------ - Checking crontab and cronjob files [ DONE ] - Checking atd status [ RUNNING ] - Checking at users [ DONE ] - Checking at jobs [ NONE ] [+] Accounting ------------------------------------ - Checking accounting information [ NOT FOUND ] - Checking sysstat accounting data [ NOT FOUND ] - Checking auditd [ NOT FOUND ] [+] Time and Synchronization ------------------------------------ [+] Cryptography ------------------------------------ - Checking for expired SSL certificates [0/3] [ NONE ] [+] Virtualization ------------------------------------ [+] Containers ------------------------------------ [+] Security frameworks ------------------------------------ - Checking presence AppArmor [ FOUND ] - Checking AppArmor status [ UNKNOWN ] - Checking presence SELinux [ NOT FOUND ] - Checking presence TOMOYO Linux [ NOT FOUND ] - Checking presence grsecurity [ NOT FOUND ] - Checking for implemented MAC framework [ NONE ] [+] Software: file integrity ------------------------------------ - Checking file integrity tools - Checking presence integrity tool [ NOT FOUND ] [+] Software: System tooling ------------------------------------ - Checking automation tooling - Ansible artifact [ FOUND ] - Automation tooling [ FOUND ] - Checking for IDS/IPS tooling [ NONE ] [+] Software: Malware ------------------------------------ [+] File Permissions ------------------------------------ - Starting file permissions check [+] Home directories ------------------------------------ - Checking shell history files [ OK ] [+] Kernel Hardening ------------------------------------ - Comparing sysctl key pairs with scan profile - fs.suid_dumpable (exp: 0) [ DIFFERENT ] - kernel.core_uses_pid (exp: 1) [ DIFFERENT ] - kernel.ctrl-alt-del (exp: 0) [ OK ] - kernel.dmesg_restrict (exp: 1) [ DIFFERENT ] - kernel.kptr_restrict (exp: 2) [ DIFFERENT ] - kernel.randomize_va_space (exp: 2) [ OK ] - kernel.sysrq (exp: 0) [ DIFFERENT ] - kernel.yama.ptrace_scope (exp: 1 2 3) [ OK ] - net.ipv4.conf.all.accept_redirects (exp: 0) [ DIFFERENT ] - net.ipv4.conf.all.accept_source_route (exp: 0) [ OK ] - net.ipv4.conf.all.bootp_relay (exp: 0) [ OK ] - net.ipv4.conf.all.forwarding (exp: 0) [ OK ] - net.ipv4.conf.all.log_martians (exp: 1) [ DIFFERENT ] - net.ipv4.conf.all.mc_forwarding (exp: 0) [ OK ] - net.ipv4.conf.all.proxy_arp (exp: 0) [ OK ] - net.ipv4.conf.all.rp_filter (exp: 1) [ DIFFERENT ] - net.ipv4.conf.all.send_redirects (exp: 0) [ DIFFERENT ] - net.ipv4.conf.default.accept_redirects (exp: 0) [ DIFFERENT ] - net.ipv4.conf.default.accept_source_route (exp: 0) [ DIFFERENT ] - net.ipv4.conf.default.log_martians (exp: 1) [ DIFFERENT ] - net.ipv4.icmp_echo_ignore_broadcasts (exp: 1) [ OK ] - net.ipv4.icmp_ignore_bogus_error_responses (exp: 1) [ OK ] - net.ipv4.tcp_syncookies (exp: 1) [ OK ] - net.ipv4.tcp_timestamps (exp: 0 1) [ OK ] - net.ipv6.conf.all.accept_redirects (exp: 0) [ DIFFERENT ] - net.ipv6.conf.all.accept_source_route (exp: 0) [ OK ] - net.ipv6.conf.default.accept_redirects (exp: 0) [ DIFFERENT ] - net.ipv6.conf.default.accept_source_route (exp: 0) [ OK ] [+] Hardening ------------------------------------ - Installed compiler(s) [ FOUND ] - Installed malware scanner [ NOT FOUND ] [+] Custom Tests ------------------------------------ - Running custom tests... [ NONE ] [+] Plugins (phase 2) ------------------------------------ ================================================================================ -[ Lynis 2.7.5 Results ]- Warnings (2): ---------------------------- ! Version of Lynis is very old and should be updated [LYNIS] https://cisofy.com/lynis/controls/LYNIS/ ! Reboot of system is most likely needed [KRNL-5830] - Solution : reboot https://cisofy.com/lynis/controls/KRNL-5830/ Suggestions (24): ---------------------------- * Set a password on GRUB bootloader to prevent altering boot configuration (e.g. boot in single user mode without password) [BOOT-5122] https://cisofy.com/lynis/controls/BOOT-5122/ * Run pwck manually and correct any errors in the password file [AUTH-9228] https://cisofy.com/lynis/controls/AUTH-9228/ * Install a PAM module for password strength testing like pam_cracklib or pam_passwdqc [AUTH-9262] https://cisofy.com/lynis/controls/AUTH-9262/ * Configure minimum password age in /etc/login.defs [AUTH-9286] https://cisofy.com/lynis/controls/AUTH-9286/ * Configure maximum password age in /etc/login.defs [AUTH-9286] https://cisofy.com/lynis/controls/AUTH-9286/ * Default umask in /etc/login.defs could be more strict like 027 [AUTH-9328] https://cisofy.com/lynis/controls/AUTH-9328/ * To decrease the impact of a full /home file system, place /home on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/ * To decrease the impact of a full /tmp file system, place /tmp on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/ * To decrease the impact of a full /var file system, place /var on a separate partition [FILE-6310] https://cisofy.com/lynis/controls/FILE-6310/ * Disable drivers like USB storage when not used, to prevent unauthorized storage or data theft [STRG-1840] https://cisofy.com/lynis/controls/STRG-1840/ * Install debsums utility for the verification of packages with known good database. [PKGS-7370] https://cisofy.com/lynis/controls/PKGS-7370/ * Install package apt-show-versions for patch management purposes [PKGS-7394] https://cisofy.com/lynis/controls/PKGS-7394/ * Install a package audit tool to determine vulnerable packages [PKGS-7398] https://cisofy.com/lynis/controls/PKGS-7398/ * Consider running ARP monitoring software (arpwatch,arpon) [NETW-3032] https://cisofy.com/lynis/controls/NETW-3032/ * Add a legal banner to /etc/issue, to warn unauthorized users [BANN-7126] https://cisofy.com/lynis/controls/BANN-7126/ * Add legal banner to /etc/issue.net, to warn unauthorized users [BANN-7130] https://cisofy.com/lynis/controls/BANN-7130/ * Enable process accounting [ACCT-9622] https://cisofy.com/lynis/controls/ACCT-9622/ * Enable sysstat to collect accounting (no results) [ACCT-9626] https://cisofy.com/lynis/controls/ACCT-9626/ * Enable auditd to collect audit information [ACCT-9628] https://cisofy.com/lynis/controls/ACCT-9628/ * Check output of aa-status [MACF-6208] - Details : /sys/kernel/security/apparmor/profiles - Solution : Run aa-status https://cisofy.com/lynis/controls/MACF-6208/ * Install a file integrity tool to monitor changes to critical and sensitive files [FINT-4350] https://cisofy.com/lynis/controls/FINT-4350/ * One or more sysctl values differ from the scan profile and could be tweaked [KRNL-6000] - Solution : Change sysctl value or disable test (skip-test=KRNL-6000:<sysctl-key>) https://cisofy.com/lynis/controls/KRNL-6000/ * Harden compilers like restricting access to root user only [HRDN-7222] https://cisofy.com/lynis/controls/HRDN-7222/ * Harden the system by installing at least one malware scanner, to perform periodic file system scans [HRDN-7230] - Solution : Install a tool like rkhunter, chkrootkit, OSSEC https://cisofy.com/lynis/controls/HRDN-7230/ Follow-up: ---------------------------- - Show details of a test (lynis show details TEST-ID) - Check the logfile for all details (less /tmp/lynis.log) - Read security controls texts (https://cisofy.com) - Use --upload to upload data to central system (Lynis Enterprise users) ================================================================================
2.2 Score
After scanning the system it gives us a score of 62%, along with the information from the tests which were carried out.
Lynis security scan details:
Hardening index : 62 [############ ] Tests performed : 205 Plugins enabled : 0 Components: - Firewall [V] - Malware scanner [X] Lynis modules: - Compliance status [?] - Security audit [V] - Vulnerability scan [V] Files: - Test and debug information : /tmp/lynis.log - Report data : /tmp/lynis-report.dat ================================================================================ Notice: Lynis update available Current version : 275 Latest version : 308 ================================================================================
3. Group audits in Lynis
One of the characteristics of Lynis is its ability to divide the results of the audit into groups to make the review and analysis a bit easier. These groups include:
vagrant@master:~/lynis$ ./lynis show groups accounting authentication banners boot_services containers crypto databases dns file_integrity file_permissions filesystems firewalls hardening homedirs insecure_services kernel kernel_hardening ldap logging mac_frameworks mail_messaging malware memory_processes nameservices networking php ports_packages printers_spools scheduling shells snmp squid ssh storage storage_nfs system_integrity time tooling usb virtualization webservers
The option “-tests-from-group” in Lynis allows you to carry out just the specific assigned auditing tests on any specific group. For example, if we want to just carry out the kernel and firewall security checks, we can use the following command:
vagrant@master:~/lynis$ ./lynis --tests-from-group "kernel firewalls" [ Lynis 2.7.5 ] ################################################################################ Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under the terms of the GNU General Public License. See the LICENSE file for details about using this software. 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ################################################################################ [+] Initializing program ------------------------------------ - Detecting OS... [ DONE ] - Checking profiles... [ DONE ] --------------------------------------------------- Program version: 2.7.5 Operating system: Linux Operating system name: Ubuntu Linux Operating system version: 20.04 Kernel version: 5.4.0 Hardware platform: x86_64 Hostname: master --------------------------------------------------- Profiles: /home/vagrant/lynis/default.prf Log file: /tmp/lynis.log Report file: /tmp/lynis-report.dat Report version: 1.0 Plugin directory: ./plugins --------------------------------------------------- Auditor: [Not Specified] Language: en Test category: all Test group: kernel firewalls --------------------------------------------------- - Program update status... [ WARNING ] =============================================================================== Lynis update available =============================================================================== Current version is more than 4 months old Current version : 275 Latest version : 308 Please update to the latest version. New releases include additional features, bug fixes, tests, and baselines. Download the latest version: Packages (DEB/RPM) - https://packages.cisofy.com Website (TAR) - https://cisofy.com/downloads/ GitHub (source) - https://github.com/CISOfy/lynis ===============================================================================
[+] System Tools ------------------------------------ - Scanning available tools... - Checking system binaries... [+] Plugins (phase 1) ------------------------------------ Note: plugins have more extensive tests and may take several minutes to complete - Plugins enabled [ NONE ] [+] Kernel ------------------------------------ - Checking default run level [ RUNLEVEL 5 ] - Checking CPU support (NX/PAE) CPU support: PAE and/or NoeXecute supported [ FOUND ] - Checking kernel version and release [ DONE ] - Checking kernel type [ DONE ] - Checking loaded kernel modules [ DONE ] Found 57 active modules - Checking Linux kernel configuration file [ FOUND ] - Checking default I/O kernel scheduler [ NOT FOUND ] - Checking for available kernel update [ OK ] - Checking core dumps configuration [ DISABLED ] - Checking setuid core dumps configuration [ PROTECTED ] - Check if reboot is needed [ YES ] [+] Software: firewalls ------------------------------------ - Checking iptables kernel module [ FOUND ] - Checking host based firewall [ ACTIVE ] [+] Custom Tests ------------------------------------ - Running custom tests... [ NONE ] [+] Plugins (phase 2) ------------------------------------ ================================================================================ -[ Lynis 2.7.5 Results ]- Warnings (2): ---------------------------- ! Version of Lynis is very old and should be updated [LYNIS] https://cisofy.com/lynis/controls/LYNIS/ ! Reboot of system is most likely needed [KRNL-5830] - Solution : reboot https://cisofy.com/lynis/controls/KRNL-5830/ No suggestions Follow-up: ---------------------------- - Show details of a test (lynis show details TEST-ID) - Check the logfile for all details (less /tmp/lynis.log) - Read security controls texts (https://cisofy.com) - Use --upload to upload data to central system (Lynis Enterprise users) ================================================================================ Lynis security scan details: Hardening index : 64 [############ ] Tests performed : 15 Plugins enabled : 0 Components: - Firewall [V] - Malware scanner [X] Lynis modules: - Compliance status [?] - Security audit [V] - Vulnerability scan [V] Files: - Test and debug information : /tmp/lynis.log - Report data : /tmp/lynis-report.dat ================================================================================ Notice: Lynis update available Current version : 275 Latest version : 308 ================================================================================ Skipped tests due to non-privileged mode FIRE-4508 - Check used policies of iptables chains FIRE-4512 - Check iptables for empty ruleset FIRE-4513 - Check iptables for unused rules FIRE-4586 - Check firewall logging ================================================================================ Lynis 2.7.5 Auditing, system hardening, and compliance for UNIX-based systems (Linux, macOS, BSD, and others) 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ================================================================================ [TIP]: Enhance Lynis audits by adding your settings to custom.prf (see /home/vagrant/lynis/default.prf for all settings)
3.1 Recommendations to improve your Lynis score
The Lynis software provides a list with the points to take care of in order to improve it. Many of them are easily fixed, others depend on if you need to make the change or not. Here are a few general suggestions to improve the Lynis score and increase the system’s security.
- Change ssh port. A simple step which provides a bit of protection for our system.
- Configure and use a firewall to limit unauthorized access to the system.
- Edit default headers.
- Use unique and secure passwords for every account and service.
- Configure two factor authentication to protect your user accounts and services.
- Deactivate unnecessary services and domains to minimize points of attack.
- Configure and make use of safety monitoring tools to supervise the system and receive alerts in case of suspicious activity.
- Use administrative passwords or root sources and avoid using these accounts unless absolutely necessary.
It is important to keep in mind that these recommendations are only a general guide and that the configuration of the security of your system depends on your specific requirements and network environment. We strongly advise that you follow the recommendations provided by Lynis in your exit report and consider hiring an IT security professional to help you to implement the additional security measures in your system.
Once you have carried out the changes, go back and perform another analysis to see the improvement in your score.
4. How to use Ansible to execute Lynis and automate the process
At Chakray, we carry out this process in a fully automated and personalized way. In the case of a large quantity of machines and servers the process will be done in a more appropriate and faster way via Ansible.
4.1 What tools do we need in order to automate this task and generate reports in Lynis?
The main tool that we need is Ansible.
Ansible is an automation tool that allows the system administrators to automate repetitive tasks and configure systems in a way which is secure and fast. Through the file, hosts can define everything and every one of the servers where we want to launch the audit. For the generation of personalized reports, in this case html, it is necessary to have python3 to be able to generate them.
In order to use Ansible to create reports with Lynis, you first need to have it installed and configured in your team. Then, you need to create an Ansible playbook file which will contain the instructions to use Lynis and generate a report.
vagrant@master:~/ansible-playbooks/chakray-lynis$ ls ansible.sh hosts playbook.yml reports
In order to execute the playbook, simply use the command Ansible-playbook followed by the name of the playbook file:
vagrant@master:~/ansible-playbooks/chakray-lynis$ sudo ansible-playbook -uroot --become-user=root playbook.yml
This will be carried out by Lynis in the server, and it will generate a report in the specified file. If we need to add more than one server the first thing we have to do is add a group in the file hosts and this will generate an audit for each one.
Once this process is finished, you will see that we have created a folder with the file logs for the node.
vagrant@master:~/ansible-playbooks/chakray-lynis/reports/localhost/var/log$ ls lynis-report.dat lynis.log
The Lynis registration file can be found in the directory “/var/log/lynis.log” and it contains detailed information about the scanning process and its results. This registration file is useful to revise the results of the scan and follow up on improvements made to the configuration of the security of the system. It can also be useful for diagnostics and to solve problems related to the security of the system.
vagrant@master:~/ansible-playbooks/chakray-lynis/reports/localhost/var/lo g$ cat lynis.log 2023-02-11 13:22:06 Starting Lynis 3.0.8 with PID 64012, build date 2022-05-17 2023-02-11 13:22:06 ==== 2023-02-11 13:22:06 ### 2007-2021, CISOfy - https://cisofy.com/lynis/ ### 2023-02-11 13:22:06 Checking permissions of /home/vagrant/ansible-playbooks/chakray-lynis/lynis/include/profiles 2023-02-11 13:22:06 File permissions are OK 2023-02-11 13:22:06 Reading profile/configuration /home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf 2023-02-11 13:22:06 Action: created temporary file /tmp/lynis.Mt4I3rhuK9 2023-02-11 13:22:06 Language set via profile to '' 2023-02-11 13:22:06 Plugin 'authentication' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'compliance' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'configuration' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'control-panels' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'crypto' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'dns' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'docker' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'file-integrity' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'file-systems' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'firewalls' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'forensics' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'hardware' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'intrusion-detection' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'intrusion-prevention' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'kernel' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'malware' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'memory' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'nginx' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'pam' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'processes' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'security-modules' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'software' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'system-integrity' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'systemd' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:06 Plugin 'users' enabled according profile (/home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf) 2023-02-11 13:22:07 Set option to default value: NTPD_ROLE --> client 2023-02-11 13:22:07 ==== 2023-02-11 13:22:07 EOL check: 0 2023-02-11 13:22:07 Program version: 3.0.8 2023-02-11 13:22:07 Operating system: Linux 2023-02-11 13:22:07 Operating system name: Ubuntu 2023-02-11 13:22:07 Operating system version: 20.04 2023-02-11 13:22:07 Kernel version: 5.4.0 2023-02-11 13:22:07 Kernel version (full): 5.4.0-62-generic 2023-02-11 13:22:07 Hardware platform: x86_64 2023-02-11 13:22:07 ----------------------------------------------------- 2023-02-11 13:22:07 Hostname: master 2023-02-11 13:22:07 Auditor: [Not Specified] 2023-02-11 13:22:07 Profiles: /home/vagrant/ansible-playbooks/chakray-lynis/lynis/default.prf 2023-02-11 13:22:07 Work directory: /home/vagrant/ansible-playbooks/chakray-lynis/lynis 2023-02-11 13:22:07 Include directory: /home/vagrant/ansible-playbooks/chakray-lynis/lynis/include 2023-02-11 13:22:07 Plugin directory: ./plugins 2023-02-11 13:22:07 ----------------------------------------------------- 2023-02-11 13:22:07 Log file: /var/log/lynis.log 2023-02-11 13:22:07 Report file: /var/log/lynis-report.dat 2023-02-11 13:22:07 Report version: 1.0 2023-02-11 13:22:07 ----------------------------------------------------- 2023-02-11 13:22:07 Test category: all 2023-02-11 13:22:07 Test group: all 2023-02-11 13:22:07 BusyBox used: 0 2023-02-11 13:22:07 ==== 2023-02-11 13:22:07 Test: Checking for program update... 2023-02-11 13:22:07 Current installed version : 308 2023-02-11 13:22:07 Latest stable version : 308 2023-02-11 13:22:07 No Lynis update available. 2023-02-11 13:22:07 Suggestion: This release is more than 4 months old. Check the website or GitHub to see if there is an update available. [test:LYNIS] [details:-] [solution:-] 2023-02-11 13:22:07 ==== 2023-02-11 13:22:07 Checking permissions of /home/vagrant/ansible-playbooks/chakray-lynis/lynis/include/binaries 2023-02-11 13:22:07 File permissions are OK 2023-02-11 13:22:07 ==== 2023-02-11 13:22:07 Action: Performing tests from category: System tools 2023-02-11 13:22:07 Start scanning for available audit binaries and tools... 2023-02-11 13:22:07 ==== ... 2023-02-11 13:22:50 ==== 2023-02-11 13:22:50 Action: Performing tests from category: Custom tests 2023-02-11 13:22:50 Test: Checking for tests_custom file 2023-02-11 13:22:50 ==== 2023-02-11 13:22:50 Action: Performing plugin tests 2023-02-11 13:22:50 Result: Found 2 plugins of which 2 are enabled 2023-02-11 13:22:50 Result: Plugins phase 2 finished 2023-02-11 13:22:50 Checking permissions of /home/vagrant/ansible-playbooks/chakray-lynis/lynis/include/report 2023-02-11 13:22:50 File permissions are OK 2023-02-11 13:22:50 Hardening index : [60] [############ ] 2023-02-11 13:22:50 Hardening strength: System has been hardened, but could use additional hardening 2023-02-11 13:22:50 ==== 2023-02-11 13:22:51 Checking permissions of /home/vagrant/ansible-playbooks/chakray-lynis/lynis/include/tool_tips 2023-02-11 13:22:51 File permissions are OK 2023-02-11 13:22:51 Tool tips: enabled 2023-02-11 13:22:51 ================================================================================ 2023-02-11 13:22:51 Tests performed: 263 2023-02-11 13:22:51 Total tests: 463 2023-02-11 13:22:51 Active plugins: 2 2023-02-11 13:22:51 Total plugins: 2 2023-02-11 13:22:51 ================================================================================ 2023-02-11 13:22:51 Lynis 3.0.8 2023-02-11 13:22:51 2007-2021, CISOfy - https://cisofy.com/lynis/ 2023-02-11 13:22:51 Enterprise support available (compliance, plugins, interface and tools) 2023-02-11 13:22:51 Program ended successfully 2023-02-11 13:22:51 ================================================================================ 2023-02-11 13:22:51 PID file removed (/var/run/lynis.pid) 2023-02-11 13:22:51 Temporary files: /tmp/lynis.Mt4I3rhuK9 /tmp/lynis.QH6PlRW8MR /tmp/lynis.2PJaxXJl4f /tmp/lynis.Kk63v57XeV 2023-02-11 13:22:51 Action: removing temporary file /tmp/lynis.Mt4I3rhuK9 2023-02-11 13:22:51 Info: temporary file /tmp/lynis.QH6PlRW8MR was already removed 2023-02-11 13:22:51 Info: temporary file /tmp/lynis.2PJaxXJl4f was already removed 2023-02-11 13:22:51 Action: removing temporary file /tmp/lynis.Kk63v57XeV 2023-02-11 13:22:51 Lynis ended successfully.
We can highlight all of the changes, applications, packages, etc. that we have in our server, information about the kernel and the changes that we need to make to improve security.
Finally, we can also see that the software provides a score on the security of our system. This case is an example of a completely empty machine and the score that it gives is 60.
2023-02-11 13:22:50 Hardening index : [60] [############ ]
This file is difficult to see in its entirety in this format, at Chakray we will provide a totally personalized report for each and every server through a script on python.
vagrant@master:~/ansible-playbooks/chakray-lynis/reports$ python3 prepare_data.py Reports generated, see index.html
This also automatically creates a report, in this case in html format.
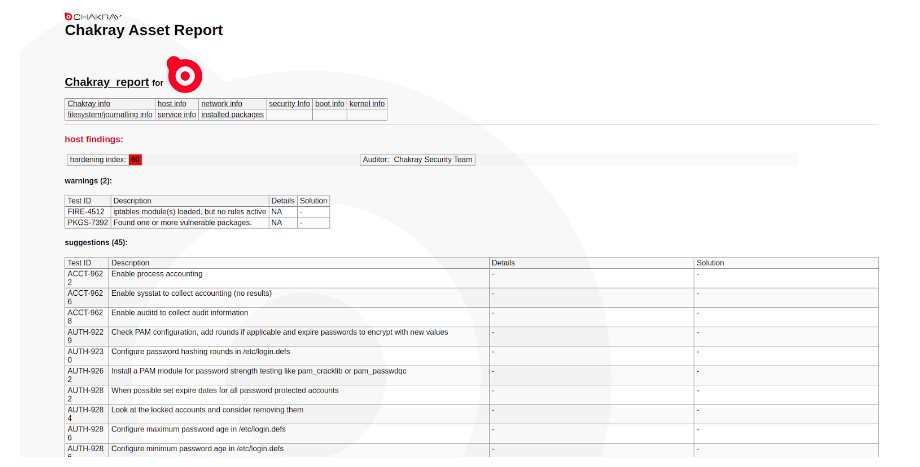
Figure 1. Chakray report
Once created, the HTML reports can be looked at online. HTML reports are useful because they allow you to present information in a way which is clear and attractive. They are also easily accessible and can be shared on the internet in a flexible way. In this way, we can see all of the suggestions which are offered to improve the security and therefore improve the score given by the report.
5. How can we improve the security of the Lynis reports?
In order to improve the security, we need to find an balance between comfort and security. The report offers us a vast array of suggestions for improvements, such as, to change the system access port, change the headings, protocols etc.
This process is called bastioning. It is the process of fortifying the security of the system by eliminating or deactivating any component or service which isn’t essential and configuring additional security measures. This should be done in order to minimize the risk of the system being attacked or compromised by an attacker. This process can be done through a bastion script system, this is a set of instructions which are carried out automatically in order to implement the security measures in the Linux system.
Once this is done, the bastion script will go back to creating reports to verify the security again and so that we can see how the score has improved.
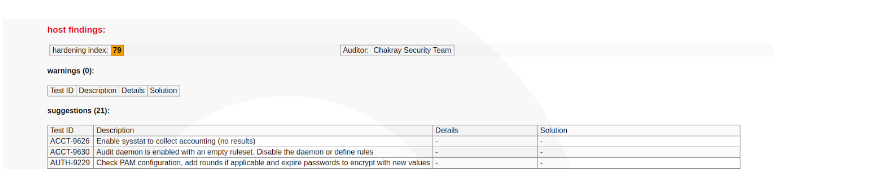
Figure 2. Host findings
We have improved the security to 79%, this will provide us with a list of suggestions again and we can assess whether they are necessary. These changes can be made manually.
6. Conclusion
In summary, using Ansible to generate reports with Lynis is an efficient and easy way to automate the auditing and security evaluation of systems. With a simple configuration you can use Ansible to execute Lynis automatically in various servers and compile reports in a centralized ad effortless way. This allows you to save time when it comes to evaluating the security of your systems, as well as helping you to maintain a clear and up-to-date vision of your security status.
With the help of Chakray this can be done in a way which is automated, for if you have a group of servers, and comfortable thanks to the personalized reports. If you would like more information, feel free to get in contact with us.